Short link for this page: utwente.nl/mfa.
TO KEEP YOUR DATA SAFE, MULTI-FACTOR AUTHENTICATION (MFA), COMPARABLE TO TWO-FACTOR AUTHENTICATION (2FA), IS NECESSARY FOR UT SYSTEMS.
Passwords can be easily compromised. MFA immediately increases your account security by requiring multiple types of verification to prove your identity when signing into an application. In general, two important situations can be considered when having trouble with the MFA:

Use the MFA reset tool in these situations: it will send a reset link to your (private) email address. Registration of a correct email address in MyHR (employees) or Studielink (students) is required.
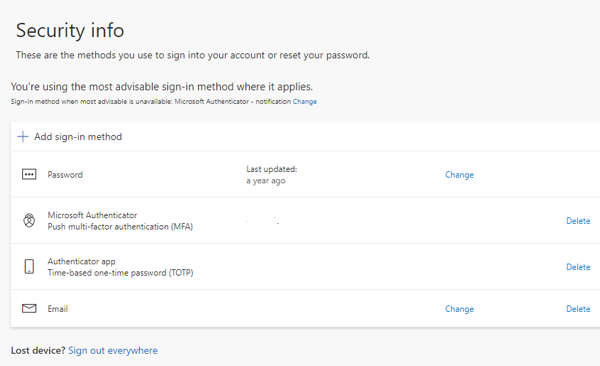
(1) Whenever you still have access to the authenticator and you wish to transfer MFA to another device or change settings, or (2) when switching to a new phone (select Add method) before disposing of the old phone.
Manuals
- These manuals are written for employees, students and x-accounts.
- You need a smartphone with Android or iOS.
- You need a UT e-mail address (x-account => x1234567@utwente.nl) and password.
- These manuals use a consistent style of writing: references to text and buttons on screens are printed in italics, information that you have to enter yourself is printed in bold.
- Multi-Factor Authentication - App Manual students & employees (incl. guest registration)
When switching to a new phone, make sure to add it here (select Add method) before deleting the Microsoft Authenticator app on your old phone.
Set up Multi-Factor Authentication
Open an application for which Multi Factor Authentication is enabled (or click here). Log in with your UT e-mail address (x-account => x1234567@utwente.nl) and password. Next you will see the following message:

Click Next and download and install the Microsoft Authenticator app on your phone (Android, iOS)
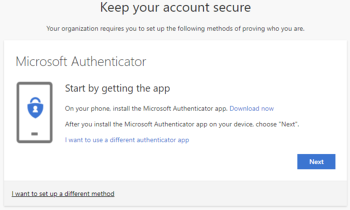
Open the Microsoft Authenticator app on your phone and click Next on the pc.
Allow the app to access the camera and add an account. Select Work or School and click Next on the pc.

Scan the QR code displayed on the pc with your phone and click Next.

A test notification is sent, please unlock your phone with fingerprint, face, or PIN and approve. If successful, you will see the following message:
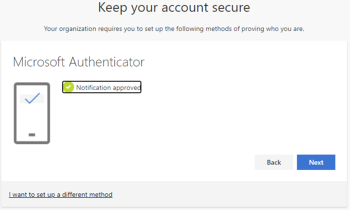
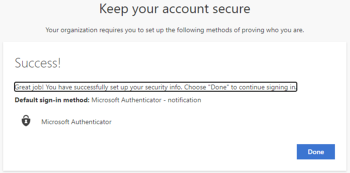
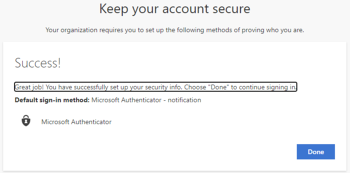
Click Next, the Microsoft Authenticator app is configured. Click Done in the next screen to continue signing in.
- Multi-Factor Authentication - App Manual UT guest
When switching to a new phone, make sure to add it here (select Add method) before deleting the Microsoft Authenticator app on your old phone. If you don't have access to your old phone you can visit the Servicedesk ICT to reset MFA (upon presentation of ID/passport/driving license). If it concerns a Teams guest account, the team owner can ask us to remove the acocunt in the UT environment and send you a new invitation.
Set up Multi-Factor Authentication
Open an application for which Multi Factor Authentication is enabled. Log in with your e-mail address and password. Next you will see the following message:

Click Next and download and install the Microsoft Authenticator app on your phone (Android, iOS)
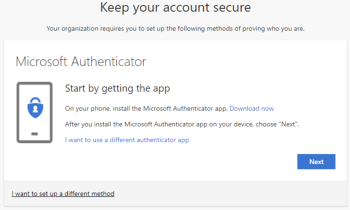
Open the Microsoft Authenticator app on your phone and click Next on the pc.
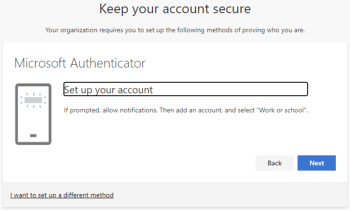
When prompted, allow notifications. Then add an account, and select “other account (Google, Facebook, etc.)"
Scan the QR code displayed on the pc with your phone and click Next.
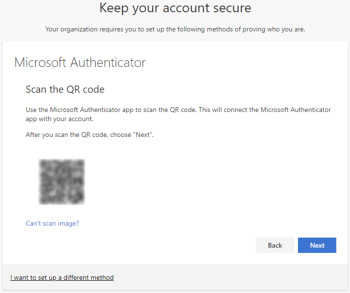
Click Next.
A test notification is sent, please unlock your phone with fingerprint, face, or PIN and approve. If successful, you will see the following message:
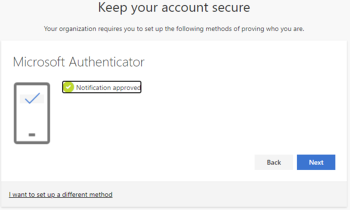
Click Next, the Microsoft Authenticator app is configured. Click Done in the next screen to continue signing in.
- Multi-Factor Authentication - Yubico FIDO2 security key
There are 2 ways to set up a FIDO2 security key as a sign-in method:
- As an additional method
- As the single method
Note: Adding a Yubico FIDO2 security key on MacOS or Linux only works with Google Chrome browser.
Add yubico fido2 security key As an additional method
- Place the FIDO2 key correctly in the USB port with the sensor facing up.
- Go to https://mysignins.microsoft.com and select Add method. Select Security key and choose Add. Approval may be requested.
- Select USB device and click Next to set the security key. Select Next/OK in the following screens until a PIN needs to be set or entered.
- Create a new PIN code (and remember it!) or enter an already set PIN code. Put your finger on the security key (2x when a new PIN code has been created) and then enter a name.
- Click Done to finish adding the security key.
- Reset security key in Windows
- Download and install YubiKey Manager.
- Insert your YubiKey into an available USB port on your computer.
- Open the YubiKey manager (administrator rights are required).
- Navigate to Applications > FIDO2.
- Click Reset FIDO, then YES.
- Follow the prompts from YubiKey Manager to remove, re-insert, and touch your key.
ADD YUBICO FIDO2 SECURITY KEY AS the single method
Note: do not us an InPrivate/incognito browser window.
- Go to https://mfa-reset.utwente.nl and click Continue. A temporary access pass code will be sent to your private e-mail address that’s registered at the University of Twente.
- Go to https://mysignins.microsoft.com/security-info and enter your UT email address. Select Use Temporary Access pass and enter the code that was sent.
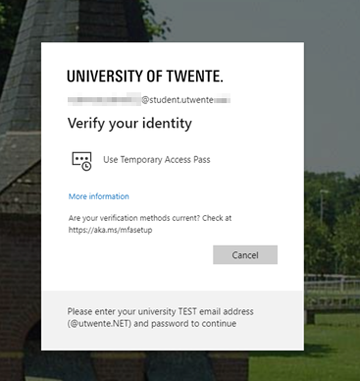
- Click + Add sign-in method, and select Security key from the dropdown menu.
- Click Add and select USB device. Plug in the FIDO2 security key and select Next. Your device will redirect you to a new window to continue the security key setup.
- In the pop up window, select Windows Hello or External Security Key. Click OK in the next window (this window may appear twice).
- Select Security key and OK twice.
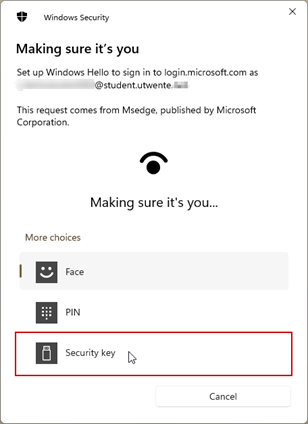
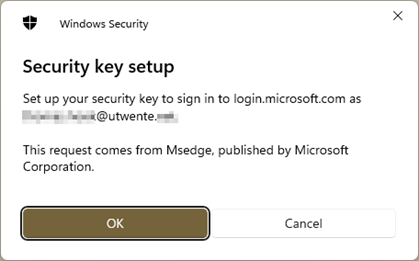
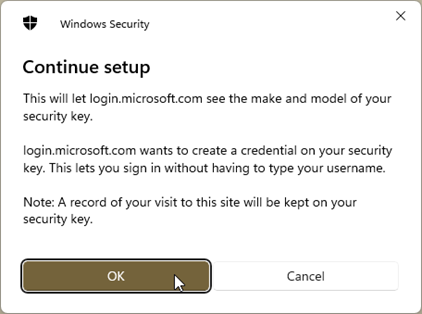
- Now you have to create a PIN code for the FIDO2 security key and confirm it by touching the security key.

- After setting up your security key you will return to the Mysignins website. Please enter a name for the security key and click next. Click Done to complete the setup.
- To log in to UT apps: plug in the security key, enter your email address and password, enter the PIN of the security key and touch it with your fingertip.
- Two-Factor verification in Google Apps for students
2-Step Verification (also commonly known as two factor authentication) is an authentication technique in which you require two separate steps to authenticate yourself (i.e. your credentials and a code you receive via your phone). This increases the security level of your account.
Why do you want to activate 2-Step Verification? For certain Google services, like an application specific password (which is necessary to import your student mail into an e-mail client), 2-Step Verification should be activated for your Google account.
Step 1: Select account
- Browse to https://googleapps.utwente.nl/ and login with your student credentials.
- In the right upper corner, click on the Google Account Button (the most right circular button).
- Click on My Account to access your student mail account.
Step 2: My account
- Click on Sign-in & security.
Step 3: Sign-in and security
- Scroll a bit down and click on the arrow on the right of 2-Step Verification.
Step 4: 2-step verification
- Click on GET STARTED.
Step 5: Phone number
- Enter your phone number in the form field. Make sure only you have access to this phone number. Use e.g. your mobile phone number for 2-Step Verification.
- Select how you want to receive the security codes: Text message (SMS) or Phone call
- Click NEXT
Step 6: receive security code
Google will now send you a security code to verify the phone number you entered in STEP 5.
- Enter this code in the form field. NOTE: Security codes are private and should never be shared with anyone, not even UT-staff or Google personnel.
- Click NEXT
Step 7: Turn on 2-step verification
- Click TURN ON to turn on 2-Step Verification.
Now 2-Step Verification is activated and you are able to generate application specific passwords.
FAQ
- Can I reset MFA myself?
Employees and students can reset their MFA through mfa-reset.utwente.nl and don't need to contact the Servicedesk ICT (except when no private email address is registered).
Guests can visit the Servicedesk ICT to reset MFA (upon presentation of ID/passport/driving license). If it concerns a Teams guest account, the team owner can ask us to remove the acocunt in the UT environment and send you a new invitation.
This answers my question.Thank you for your feedback - Why is Multi-Factor Authentication necessary?
In the General Data Protection Regulation (GDPR), the criteria set for processing special personal data have been tightened. Special personal data is highly sensitive and therefore receives additional protection under the GDPR. Logging in with a username and password is no longer sufficient.
The UT utilises multiple applications within which personal data is processed. The GDPR stipulates that these applications are additionally secured by means of authentication in two steps: MFA.Programmes may contain data to which others are not permitted access. This may include research data, examination results, or bank account numbers. Passwords can be found out with relative ease, for example when you:
- use the same password for multiple websites;
- download malicious software from the internet;
- accidentally activate incorrect links in a phishing email;
- provide your password to others.
Thanks to additional authentication, the university can exclude information from unwanted individuals, even when they possess your password. For this reason, your additional authentication is for personal use only.
This answers my question.Thank you for your feedback - What is the risk of others knowing my password?
An individual in possession of your password can block access to your account and:
- view or even delete your emails, contacts, and educational or research data;
- masquerade as you and send unsolicited or malicious emails to your contacts;
- use your account to reset the passwords for your other accounts;
- gain access to all information accessible to you, such as student data.
This answers my question.Thank you for your feedback - Can I reduce the MFA approval messages?
We have the following tip:
- Use Microsoft Edge as your browser. Click on the profile icon at the right side of the address bar and click "Sign In." Then, sign in with your work or school account.
This answers my question.Thank you for your feedback - How do I set up my private e-mail address for MFA reset? (employees)
- Go to settings MyHR (myhr.utwente.nl)
- Click on 'my file'
- 'My personal details'
- Then go to 'change personal data' and add your personal email address under Private contact data.
This answers my question.Thank you for your feedback
Mobile telephone
- I don't want to use my private telephone for work. How can I log in with MFA? (employees)
If the UT has not provided you with a mobile telephone and you don't wish to use a private smartphone for the MFA, you can obtain a low-budget mobile telephone via the LISA self-service portal. The charges will be covered by the faculty/service department. You will need a work order number from your organisation for ordering a low-budget telephone.
This answers my question.Thank you for your feedback - I don't have an internet connection on my mobile telephone, will the app still work?
An internet connection (WiFi/4G/5G) is only required for app installation/activation and number matching. Once set, you can also use the time-based, one-time passcode in the app.
During offline use, the Microsoft Authenticator app automatically creates an offline code which can be entered on your screen. This allows you to use the additional authentication offline at all times.
This answers my question.Thank you for your feedback - Why am I unable to scan the QR code?
Tips for successful QR code scanning:
- Zoom level of PC browser set to minimum 100%
- While scanning, do not hold the device too close to the screen! Make sure that the QR code fills approx. 25% of the screen. Hold the device still!
- Hold your smartphone very still while scanning. Your smartphone may need a few moments for scanning, as the camera must first zoom in on the QR code.
- Ensure that only the QR code is in the frame when scanning.
- Keep any objects, such as your finger, from obstructing the camera during scanning.
- Increase the brightness of your computer screen. This increases the contrast of the QR code, making it easier for your camera to scan.
This answers my question.Thank you for your feedback - My smartphone is at home and I cannot log in to additionally secured systems now. What should I do?
- Collect your smartphone, if possible.
- If the organisation has a spare smartphone, it can be used temporarily. Go to mfa-reset.utwente.nl to reset MFA and set it up again.
This answers my question.Thank you for your feedback - When do I have to validate again with MFA?
You must re-validate MFA:
- after you have changed from workstation/browser
- after you have changed your password
- if you did not use your workstation/browser for a period of 90 days
* To reduce the number of approvals in a browser, you can use the Edge browser and log in with your UT account.
This answers my question.Thank you for your feedback - Can I disable the use of fingerprint, face, or PIN with every prompt for authentication?
Yes, you can disable it in the settings in the Microsoft Authenticator app.
This answers my question.Thank you for your feedback - I don't receive a notification from the app
Sometimes it happens that no message appears. In this case, you can log in to the app with the one-time passcode (tap your UT email address for the code).
This answers my question.Thank you for your feedback
Authentication, verfication, etc.
- Can I authorise someone else to log in on my behalf?
No, this is not possible. MFA is for personal use only and cannot be transferred.
This answers my question.Thank you for your feedback - What is number matching?
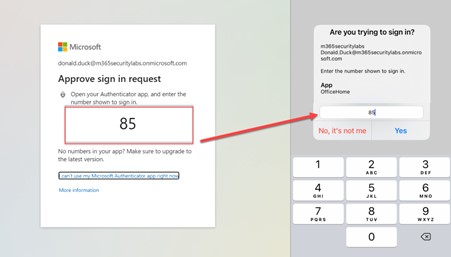
Microsoft has found criminals to use something called MFA fatigue attacks. When criminals have a user's credentials, they usually can't access the account because of MFA. In an MFA fatigue attack, the criminal will try to log in frequently in a very short period.
The criminal expects the user to get weary of the number of requests from the authentication app. The user might think it is a request generated by his Outlook app or Teams. At one point, the user will confirm the request and unwittingly give the criminal access to their account.
The Microsoft Authenticator (shown on the right) displays information about the application and asks you to enter a two-digit number. The Single Sign-On page will give you a number when logging in (as shown in the left picture below). After you copy the number, the login process will continue.
 This answers my question.Thank you for your feedback
This answers my question.Thank you for your feedback
Contact

Visit us: 8.30 - 17.00 on weekdays (location)
Call us: 8.00 - 17.00 on weekdays
To support you on the phone, we may ask you to open Teamviewer. The application has already been installed on UT Windows computers. For other devices, you may need to download Teamviewer.